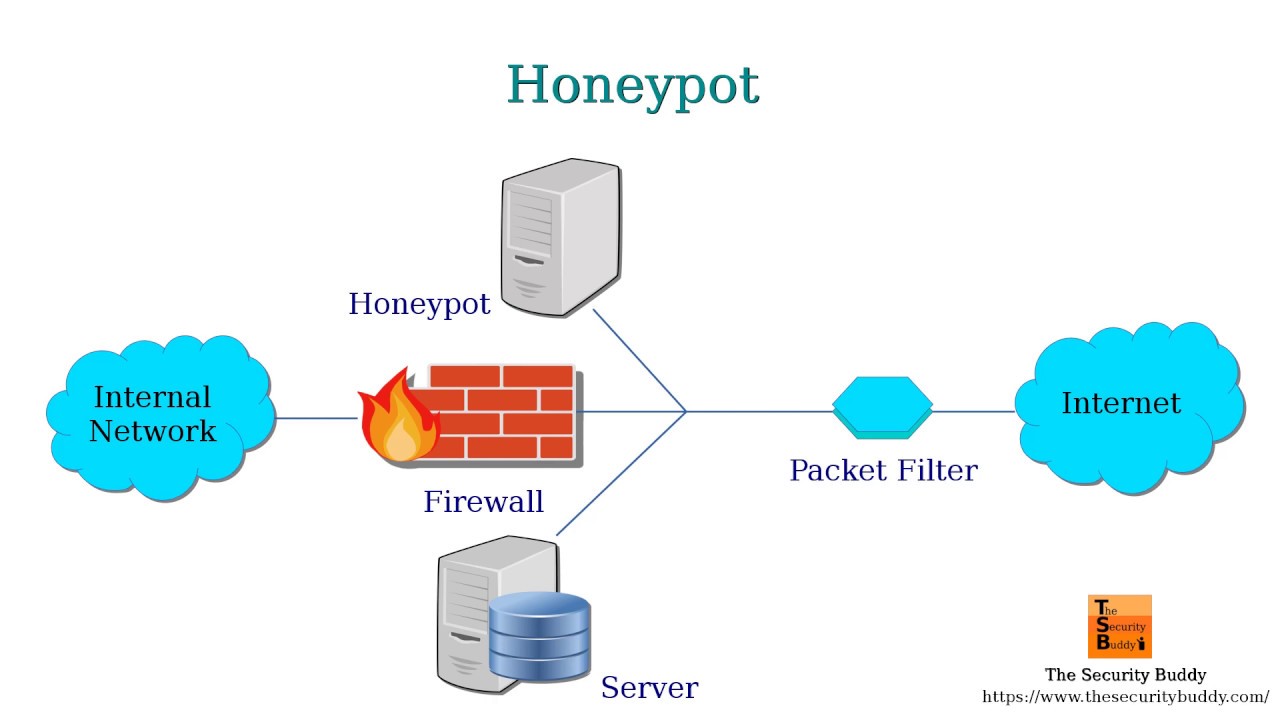
The first step in setting up a Honeypot is to decide on the type of Honeypot to use. This decision will depend on the specific goals of the Honeypot and the resources available. For example, if the goal is to collect data on malware attacks, a Honeypot that mimics a vulnerable system may be used.. Examining the trade history is one technique to recognize a honeypot crypto fraud. A cryptocurrency should generally allow you to buy and sell it whenever you desire. There will be a lot of buys.

Honey for money Make money from honey bees How much money you can make with honey bees
Data Security Innovation RouserNews

“Make Honey. Get Money.” Sticker for Sale by itskonnerwithak Redbubble
Saving money with the honey app
Honey

What is Honeygain and is Honeygain legit? by HorrorReaper Medium

How To Save Loads Of Money With Honey Browser Extension

Making Money, Honey Pricing Your Honey LeaseHoney

Cash**App Real Giftcard Legit way in 2022 How to get money, Free money, Free cash

How to Save Money on Almost Everything Online with Honey YouTube

How To Get Money in 40 Days easy ways to make money makemoney easy hafizusman usa

How do I get money out of my PayPal account? I get money, How to get money, How do i get

How to Spot Honeypot Scam and Get Out of it

Honey Review And Guide Can You Really Save Money With Honey?

HOW TO SAVE MONEY HONEY! YouTube

Money Honey A Simple 7Step Guide for Getting Your Financial hit Together by Rachel Richards

Does Honey Save You Money? Honey Browser Extension Review YouTube

How to take money out of Stable Fund Optimus Money Passive YouTube
How To Get Cash Out Of An ATM With Apple Pay! YouTube

Stash The Cash How To Make Lots ‘O Money Honey!
Keep your honeypot separate from your original network. Use fake, tempting data to lure your targets in. This includes fake customer details, a fake credential database, employee bank details, etc. Install firewalls to keep the intruders inside the network for as long as possible.. A honeypot is a scam used in the crypto industry to trap victims and steal their assets or sensitive information. Honeypots involve setting up a fake website or wallet that appears legitimate but is designed to lure in and deceive unwary users. For example, a scammer may create a fake wallet or a manipulated smart contract.




